Tabla de Contenidos
![]()
5.1.1 Servidor IMAP/IMAPS
Objetivo
Instalar un servidor de e-mail que soporte el protocolo IMAPS.
Instalación
root@server:~# apt-get install dovecot-imapd
Configuración
Toda la configuración está almacenada en el archivo /etc/dovecot/local.conf.
root@server:~# touch /etc/dovecot/local.conf
El servidor de e-mail dovecot sólo acepta conexiones encriptadas vía TLS (Transport Layer Security) o SSL (Secure Sockets Layer). Ambos requieren certificados digitales.
Los certificados SSL para dovecot son generados automáticamente durante la instalación. Sin embargo, podemos utilizar los Certificados ssl Auto-firmados que se generaron previamente:
- /etc/dovecot/local.conf
## ## SSL settings ## # SSL/TLS support: yes, no, required. <doc/wiki/SSL.txt> #ssl = yes # PEM encoded X.509 SSL/TLS certificate and private key. They're opened before # dropping root privileges, so keep the key file unreadable by anyone but # root. Included doc/mkcert.sh can be used to easily generate self-signed # certificate, just make sure to update the domains in dovecot-openssl.cnf #ssl_cert = </etc/dovecot/dovecot.pem #ssl_key = </etc/dovecot/private/dovecot.pem ssl_cert = </etc/ssl/certs/server.crt ssl_key = </etc/ssl/private/server.key # If key file is password protected, give the password here. Alternatively # give it when starting dovecot with -p parameter. Since this file is often # world-readable, you may want to place this setting instead to a different # root owned 0600 file by using ssl_key_password = <path. #ssl_key_password = # [...]
La localización de los buzones de correo debe indicarse también, para evitar ambigüedades. En este caso se encuentran en un sub-directorio del directorio home de cada usuario llamada “Maildir”:
- /etc/dovecot/local.conf
# [...] ## ## Mailbox locations and namespaces ## # Location for users' mailboxes. The default is empty, which means that Dovecot # tries to find the mailboxes automatically. This won't work if the user # doesn't yet have any mail, so you should explicitly tell Dovecot the full # location. # # If you're using mbox, giving a path to the INBOX file (eg. /var/mail/%u) # isn't enough. You'll also need to tell Dovecot where the other mailboxes are # kept. This is called the "root mail directory", and it must be the first # path given in the mail_location setting. # # There are a few special variables you can use, eg.: # # %u - username # %n - user part in user@domain, same as %u if there's no domain # %d - domain part in user@domain, empty if there's no domain # %h - home directory # # See doc/wiki/Variables.txt for full list. Some examples: # # mail_location = maildir:~/Maildir # mail_location = mbox:~/mail:INBOX=/var/mail/%u # mail_location = mbox:/var/mail/%d/%1n/%n:INDEX=/var/indexes/%d/%1n/%n # # <doc/wiki/MailLocation.txt> # #mail_location = mbox:~/mail:INBOX=/var/mail/%u mail_location = maildir:~/Maildir # [...]
La configuracion de puede comprobar con el comando dovecot -n:
root@server:~# dovecot -n # 2.1.7: /etc/dovecot/dovecot.conf # OS: Linux 3.2.0-4-686-pae i686 Debian 7.0 mail_location = maildir:~/Maildir namespace inbox { inbox = yes location = mailbox Drafts { special_use = \Drafts } mailbox Junk { special_use = \Junk } mailbox Sent { special_use = \Sent } mailbox "Sent Messages" { special_use = \Sent } mailbox Trash { special_use = \Trash } prefix = } passdb { driver = pam } protocols = " imap" ssl_cert = </etc/ssl/certs/server.crt ssl_key = </etc/ssl/private/server.key userdb { driver = passwd }
Las ramas del árbol Maildir debe generarse a partir del home de cada usuario. Para esto, debe ser ejecutado el comando maildirmake.dovecot por cada usuario ya creado.
El comando más abajo muda la identidad del usuario corriente para un usuario “fribeiro” y crea la rama Maildir en el home del mismo usuario. Este comando debe repetirse con cada usuario ya existente:
root@server:~# su - fribeiro -c 'maildirmake.dovecot ~/Maildir'
Esta rama también debe ser creada sobre el directorio /etc/skel. El contenido de /etc/skelse utiliza como modelo para el directorio home de los usuarios que sean creados en el futuro. Así, cuando se activaran nuevos usuarios, las ramas de Maildir se generarían automáticamente:
root@server:~# maildirmake.dovecot /etc/skel/Maildir
Reiniciar el servidor:
root@server:~# service dovecot restart
Verificación
Verificar el servicio imap para las direcciones locales:
root@server:~# telnet 127.0.0.1 imap Trying 127.0.0.1... Connected to 127.0.0.1. Escape character is '^]'. * OK [CAPABILITY IMAP4rev1 LITERAL+ SASL-IR LOGIN-REFERRALS ID ENABLE IDLE STARTTLS AUTH=PLAIN] Dovecot ready. a001 login fribeiro password a001 OK [CAPABILITY IMAP4rev1 LITERAL+ SASL-IR LOGIN-REFERRALS ID ENABLE IDLE SORT SORT=DISPLAY THREAD=REFERENCES THREAD=REFS MULTIAPPEND UNSELECT CHILDREN NAMESPACE UIDPLUS LIST-EXTENDED I18NLEVEL=1 CONDSTORE QRESYNC ESEARCH ESORT SEARCHRES WITHIN CONTEXT=SEARCH LIST-STATUS SPECIAL-USE] Logged in a002 examine inbox * FLAGS (\Answered \Flagged \Deleted \Seen \Draft) * OK [PERMANENTFLAGS ()] Read-only mailbox. * 0 EXISTS * 0 RECENT * OK [UIDVALIDITY 1368467911] UIDs valid * OK [UIDNEXT 1] Predicted next UID * OK [NOMODSEQ] No permanent modsequences a002 OK [READ-ONLY] Select completed. a003 logout * BYE Logging out a003 OK Logout completed. Connection closed by foreign host.
Desde otro sistema, verificar si son rechazadas las conexiones IMAP simples sim TLS por ser consideradas inseguras, una vez se envíen las contraseñas en texto simple:
fribeiro@laptop:~$ telnet 192.168.1.100 imap Trying 192.168.1.100... Connected to 192.168.1.100. Escape character is '^]'. * OK [CAPABILITY IMAP4rev1 LITERAL+ SASL-IR LOGIN-REFERRALS ID ENABLE IDLE STARTTLS AUTH=PLAIN] Dovecot ready. a001 login fribeiro password * BAD Error in IMAP command received by server. a002 logout * BYE Logging out a002 OK Logout completed. Connection closed by foreign host.
Sin embargo, las conexiones IMAPS deben ser aceptadas a partir de cualquier sistema:
fribeiro@laptop:~# openssl s_client -connect 192.168.1.100:imaps CONNECTED(00000003) depth=0 C = PT, ST = Portugal, O = My Home Lan, CN = *.home.lan verify error:num=18:self signed certificate verify return:1 depth=0 C = PT, ST = Portugal, O = My Home Lan, CN = *.home.lan verify return:1 --- Certificate chain 0 s:/C=PT/ST=Portugal/O=My Home Lan/CN=*.home.lan i:/C=PT/ST=Portugal/O=My Home Lan/CN=*.home.lan --- Server certificate -----BEGIN CERTIFICATE----- MIIDEjCCAfoCCQD5SP5wlSUnnjANBgkqhkiG9w0BAQUFADBLMQswCQYDVQQGEwJQ VDERMA8GA1UECAwIUG9ydHVnYWwxFDASBgNVBAoMC015IEhvbWUgTGFuMRMwEQYD VQQDDAoqLmhvbWUubGFuMB4XDTEzMDUwOTE4MTI0NVoXDTE0MDUwOTE4MTI0NVow SzELMAkGA1UEBhMCUFQxETAPBgNVBAgMCFBvcnR1Z2FsMRQwEgYDVQQKDAtNeSBI b21lIExhbjETMBEGA1UEAwwKKi5ob21lLmxhbjCCASIwDQYJKoZIhvcNAQEBBQAD ggEPADCCAQoCggEBAKEPpb+QzPo1YQrzm0inq7wWq4k/0QYN8Uf2XZjLyQlkPCXF abInf/io9L1/xo4s4jByh9PKh8RWd6rpGZins7VUcKhsX8tzh2yj65i0KJcum4Nx pQ3Pj61S/Nb35+XYtvR5+SsDryEBg6KGp4R1nEfeNhg8Avl7Ertn+kI0hUuIK9Ga 3XF9G9b92Se4GTs81mU0fWSd/g/A49DagwnQoHUTN08UhpkYWTEYFckKSuhciON0 qQnmR9Ws//ZABI0YR57LxkWBD+Q05355Mz5X9vPMgGtnB9r3tPzxrqkn8WYESlz0 5vTM5UfIZIqrdZAHXIHrtJi8yxf202pzOKnrACkCAwEAATANBgkqhkiG9w0BAQUF AAOCAQEAHObIFnGY0PkET5qNVnqpj8ZivT8F38B6aefokDGMDJPyvPDGPWDaVWsr XuleEwMvj4SrYYRjGHVh4M74ep+guKfNe1zJxm4PNvlfqoGsQNsLJO/CGvWPoLu5 mepFbNkNWI5GinRGFzM9g0j3aU1zUK6pkhaKtQ+4mgnirCWyo4m6d1ukaSMfDEVN nk2K5DnGgWVOy018wQe6XfqiXOscvMl8KoxkOx2kxPRZDAxWmWKnCpG+MNrw68Lz CCCbujYLCWc5xjHLlCgV6MqwSouIDtaZlP5wM7ChI9u1+rWH5Uc6eFhCW1XQ1yzG hBaB3tuM0jXYrKln1MOHPZILsCcSxQ== -----END CERTIFICATE----- subject=/C=PT/ST=Portugal/O=My Home Lan/CN=*.home.lan issuer=/C=PT/ST=Portugal/O=My Home Lan/CN=*.home.lan --- No client certificate CA names sent --- SSL handshake has read 1644 bytes and written 518 bytes --- New, TLSv1/SSLv3, Cipher is DHE-RSA-AES256-GCM-SHA384 Server public key is 2048 bit Secure Renegotiation IS supported Compression: zlib compression Expansion: zlib compression SSL-Session: Protocol : TLSv1.2 Cipher : DHE-RSA-AES256-GCM-SHA384 Session-ID: 7132EDC87DCFB31A724AA30B9DFA0228B09A9B01602F87AFED370767DD68CAA1 Session-ID-ctx: Master-Key: 43280FEF5FDEB05D5E9860C3F667B7D96BAFF33B0DE97D41E7FD8216CEF3E5D4B16EC848094B3382CBE496D49D88D6AD Key-Arg : None PSK identity: None PSK identity hint: None SRP username: None TLS session ticket lifetime hint: 300 (seconds) TLS session ticket: 0000 - 75 73 aa ca 0b 29 4b 13-fe 0a 06 44 a4 0a f1 6c us...)K....D...l 0010 - 81 a1 ec 80 15 09 7e b3-09 c3 ab 72 01 25 ea 51 ......~....r.%.Q 0020 - 97 45 95 19 0e 14 d7 21-67 57 db 3b 83 73 f0 56 .E.....!gW.;.s.V 0030 - 07 44 db 45 3f ce fa 8c-3a cc 48 22 29 7b db 43 .D.E?...:.H"){.C 0040 - fa 08 12 93 dc be 36 78-23 a4 4f 68 bb 34 71 40 ......6x#.Oh.4q@ 0050 - 6e 8c 07 44 fa 7f 77 4d-95 a0 b1 24 05 a6 08 93 n..D..wM...$.... 0060 - 79 b6 d3 e5 d0 a3 e0 db-85 7a d1 81 ae 73 1f 33 y........z...s.3 0070 - 73 24 81 10 29 ae 8f 63-8c f5 b1 2e e5 43 f6 65 s$..)..c.....C.e 0080 - 9d 2c b8 e2 7d 6b 8f 71-22 ff d7 82 fa 5d 11 56 .,..}k.q"....].V 0090 - 5f ef 39 f3 65 10 eb 17-58 ac 29 15 13 c7 b3 7c _.9.e...X.)....| Compression: 1 (zlib compression) Start Time: 1368468299 Timeout : 300 (sec) Verify return code: 18 (self signed certificate) --- * OK [CAPABILITY IMAP4rev1 LITERAL+ SASL-IR LOGIN-REFERRALS ID ENABLE IDLE AUTH=PLAIN] Dovecot ready. a001 login fribeiro password a001 OK [CAPABILITY IMAP4rev1 LITERAL+ SASL-IR LOGIN-REFERRALS ID ENABLE IDLE SORT SORT=DISPLAY THREAD=REFERENCES THREAD=REFS MULTIAPPEND UNSELECT CHILDREN NAMESPACE UIDPLUS LIST-EXTENDED I18NLEVEL=1 CONDSTORE QRESYNC ESEARCH ESORT SEARCHRES WITHIN CONTEXT=SEARCH LIST-STATUS SPECIAL-USE] Logged in a002 examine inbox * FLAGS (\Answered \Flagged \Deleted \Seen \Draft) * OK [PERMANENTFLAGS ()] Read-only mailbox. * 0 EXISTS * 0 RECENT * OK [UIDVALIDITY 1368467911] UIDs valid * OK [UIDNEXT 1] Predicted next UID * OK [NOMODSEQ] No permanent modsequences a002 OK [READ-ONLY] Select completed. a003 logout * BYE Logging out a003 OK Logout completed. closed
Configuración de los clientes
Como verificación final, puede crearse una cuenta en un cliente de e-mail, como Thunderbird: Para esto, debe seleccionarse el protocolo IMAP, la conexión requiere TLS (puerto 143) o SSL (puerto 993) y la dirección será la del servidor (192.168.1.100 o mail.home.lan, en caso de que haya configurado previamente un Servidor DNS para la red local).

Si se configuró el acceso sin TLS o SSL, el acceso será negado:

Certificados auto-firmados
Dado que los certificados son auto-firmados, en los clientes e-mail aparecerá una ventana donde consta que no conocen la autoridad del certificado.
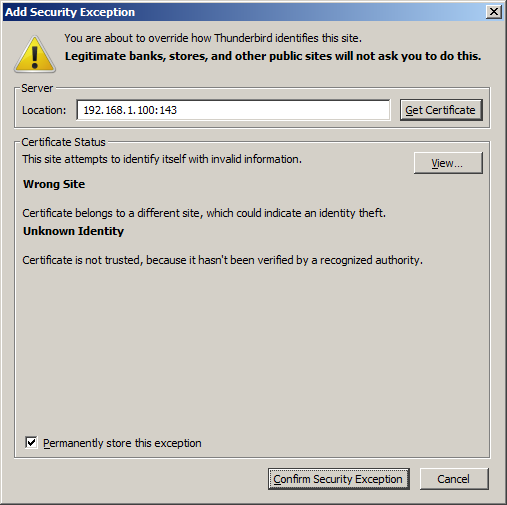
Una verificación debe indicar que el certificado utilizado es realmente el que queremos usar:
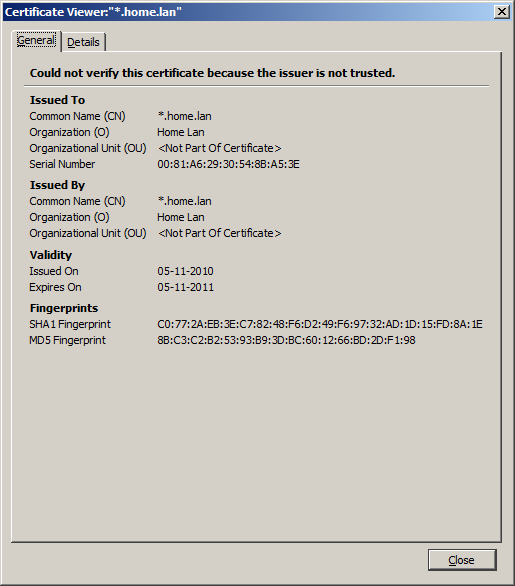
Una vez verificado el certificado, este podrá ser añadido a la lista de excepciones de seguridad.